不错呦!smile@林凯西,确保“准备文件”中的几个文件都有安装,S...您好,看了您这篇帖子觉得很有帮助。但是有个问题想请...我的修改过了怎么还被恶意注册呢 @jjjjiiii 用PJ快9年了,主要是A...PJ3啊,貌似很少有人用PJ了,现在不是WP就是z...@332347365,我当时接入时错误码没有-10...楼主,ChkValue值应为-103是什么意思呢?...大哥 你最近能看到我发的信息,请跟我联系,我有个制...
autorun病毒(PegeFile.pif/Trojan.PSW.Win32.Agent.mk)
编辑:dnawo 日期:2007-06-21
病毒名字:Trojan.PSW.Win32.Agent.mk(Rising)
样本名:PegeFile.pif
加壳:UPX
文件大小:16,945 字节
MD5:A3AEB72FCDEEB46C04936564419C7275
SHA1:0F1719C33EA1E8E0B492A00BD3049BC20FB49A26
简单写了,这个病毒其实是一个 Download 病毒,运行后会继续下载其他的病毒!(Rising命名错误)
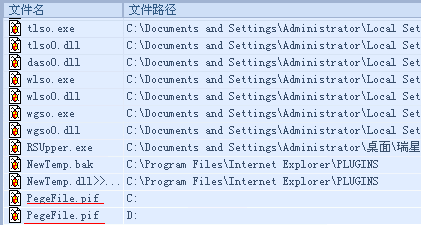
病毒运行后首先释放自己和库文件到:
C:\Program Files\Internet Explorer\PLUGINS\NewTemp.bak
C:\Program Files\Internet Explorer\PLUGINS\NewTemp.dll
向所有分区释放:
X:\PegeFile.pif
X:\autorun.inf
病毒将库文件注入到 explorer.exe 进程,伺机作案。
若是可以链接网络,它会下载以下病毒到用户的机器上,(很多。。。)
C:\DOCUME~1\TestUser\LOCALS~1\Temp\2.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\1.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\mhso.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\mhso0.dll
C:\DOCUME~1\TestUser\LOCALS~1\Temp\3.exe
C:\WINDOWS\system32\ztinetzt.exe
C:\WINDOWS\system32\ztinetzt.dll
C:\DOCUME~1\TestUser\LOCALS~1\Temp\4.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\rxso.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\rxso0.dll
C:\DOCUME~1\TestUser\LOCALS~1\Temp\5.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\6.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\qjso.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\qjso0.dll
C:\WINDOWS\system32\Ravasktao.exe
C:\WINDOWS\system32\Ravasktao.dll
C:\DOCUME~1\TestUser\LOCALS~1\Temp\7.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\tlso.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\tlso0.dll
C:\DOCUME~1\TestUser\LOCALS~1\Temp\8.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\daso.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\daso0.dll
C:\DOCUME~1\TestUser\LOCALS~1\Temp\7.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\8.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\9.exe
C:\Program Files\Internet Explorer\PLUGINS\System64.Jmp
C:\Program Files\Internet Explorer\PLUGINS\System64.Sys
C:\DOCUME~1\TestUser\LOCALS~1\Temp\10.exe
C:\WINDOWS\system32\Drivers\usbinte.sys
C:\WINDOWS\system32\visin.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\11.exe
C:\WINDOWS\system32\mydata.exe
C:\WINDOWS\system32\moyu103.dll
C:\DOCUME~1\TestUser\LOCALS~1\Temp\13.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\wlso.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\wlso0.dll
C:\DOCUME~1\TestUser\LOCALS~1\Temp\14.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\wgso.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\wgso0.dll
C:\DOCUME~1\TestUser\LOCALS~1\Temp\15.exe
C:\WINDOWS\system32\wuclmi.exe
C:\WINDOWS\system32\wincfg.exe
C:\WINDOWS\system32\mvdbc.exe
C:\WINDOWS\system32\packet.dll
C:\WINDOWS\system32\pthreadVC.dll
C:\WINDOWS\system32\wanpacket.dll
C:\WINDOWS\system32\wpcap.dll
C:\WINDOWS\system32\drivers\npf.sys
C:\WINDOWS\system32\npf_mgm.exe
C:\WINDOWS\system32\daemon_mgm.exe
C:\WINDOWS\system32\NetMonInstaller.exe
C:\WINDOWS\system32\rpcapd.exe
C:\WINDOWS\system32\capinstall.exe
修改注册表:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\Currentversion\Run
"wosa" = %TEMP%WOSO.EXE
"mhsa" = %TEMP%MHSO.EXE
"Microsoft Autorun14" = %SYSTEM%\ZTINETZT.EXE
"rxsa" = %TEMP%RXSO.EXE
"qjsa" = %TEMP%QJSO.EXE
"Microsoft Autorun9" = %SYSTEM%\RAVASKTAO.EXE
"tlsa" = %TEMP%TLSO.EXE
"dasa" = %TEMP%DASO.EXE
"wlsa" = %TEMP%WLSO.EXE
"wgsa" = %TEMP%WGSO.EXE
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\Run
"visin" = %SYSTEM%\VISIN.EXE
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\ShellExecuteHooks
"{0EA66AD2-CF26-2E23-532B-B292E22F3266}" =
"{754FB7D8-B8FE-4810-B363-A788CD060F1F}" =
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\nm
(Display Name)Network Monitor Driver = (IMAGEPATH)SYSTEM32\DRIVERS\NMNT.SYS
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NPF
(Display Name)NetGroup Packet Filter Driver = (IMAGEPATH)SYSTEM32\DRIVERS\NPF.SYS
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\rpcapd
(Display Name)Remote Packet Capture Protocol v.0 (experimental) = (IMAGEPATH)"%PROGRAMFILES%\WINPCAP\RPCAPD.EXE" -D -F "%PROGRAMFILES%\WINPCAP\RPCAPD.INI"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\nm
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\nm.sys
HKEY_LOCAL_MACHINE\Software\Classes\CLSID\{0EA66AD2-CF26-2E23-532B-B292E22F3266}
HKEY_LOCAL_MACHINE\Software\Classes\CLSID\{425882B0-B0BF-11CE-B59F-00AA006CB37D}
HKEY_LOCAL_MACHINE\Software\Classes\CLSID\{754FB7D8-B8FE-4810-B363-A788CD060F1F}
HKEY_LOCAL_MACHINE\Software\Classes\CLSID\{944AD531-B09D-11CE-B59C-00AA006CB37D}
HKEY_LOCAL_MACHINE\Software\Classes\CLSID\{D413C502-3FAA-11D0-B254-444553540000}
杀毒方法:
将瑞星病毒库升至2007-06-21后可杀,之前一直查不出来!
样本名:PegeFile.pif
加壳:UPX
文件大小:16,945 字节
MD5:A3AEB72FCDEEB46C04936564419C7275
SHA1:0F1719C33EA1E8E0B492A00BD3049BC20FB49A26
简单写了,这个病毒其实是一个 Download 病毒,运行后会继续下载其他的病毒!(Rising命名错误)
病毒运行后首先释放自己和库文件到:
C:\Program Files\Internet Explorer\PLUGINS\NewTemp.bak
C:\Program Files\Internet Explorer\PLUGINS\NewTemp.dll
向所有分区释放:
X:\PegeFile.pif
X:\autorun.inf
病毒将库文件注入到 explorer.exe 进程,伺机作案。
若是可以链接网络,它会下载以下病毒到用户的机器上,(很多。。。)
C:\DOCUME~1\TestUser\LOCALS~1\Temp\2.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\1.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\mhso.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\mhso0.dll
C:\DOCUME~1\TestUser\LOCALS~1\Temp\3.exe
C:\WINDOWS\system32\ztinetzt.exe
C:\WINDOWS\system32\ztinetzt.dll
C:\DOCUME~1\TestUser\LOCALS~1\Temp\4.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\rxso.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\rxso0.dll
C:\DOCUME~1\TestUser\LOCALS~1\Temp\5.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\6.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\qjso.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\qjso0.dll
C:\WINDOWS\system32\Ravasktao.exe
C:\WINDOWS\system32\Ravasktao.dll
C:\DOCUME~1\TestUser\LOCALS~1\Temp\7.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\tlso.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\tlso0.dll
C:\DOCUME~1\TestUser\LOCALS~1\Temp\8.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\daso.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\daso0.dll
C:\DOCUME~1\TestUser\LOCALS~1\Temp\7.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\8.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\9.exe
C:\Program Files\Internet Explorer\PLUGINS\System64.Jmp
C:\Program Files\Internet Explorer\PLUGINS\System64.Sys
C:\DOCUME~1\TestUser\LOCALS~1\Temp\10.exe
C:\WINDOWS\system32\Drivers\usbinte.sys
C:\WINDOWS\system32\visin.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\11.exe
C:\WINDOWS\system32\mydata.exe
C:\WINDOWS\system32\moyu103.dll
C:\DOCUME~1\TestUser\LOCALS~1\Temp\13.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\wlso.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\wlso0.dll
C:\DOCUME~1\TestUser\LOCALS~1\Temp\14.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\wgso.exe
C:\DOCUME~1\TestUser\LOCALS~1\Temp\wgso0.dll
C:\DOCUME~1\TestUser\LOCALS~1\Temp\15.exe
C:\WINDOWS\system32\wuclmi.exe
C:\WINDOWS\system32\wincfg.exe
C:\WINDOWS\system32\mvdbc.exe
C:\WINDOWS\system32\packet.dll
C:\WINDOWS\system32\pthreadVC.dll
C:\WINDOWS\system32\wanpacket.dll
C:\WINDOWS\system32\wpcap.dll
C:\WINDOWS\system32\drivers\npf.sys
C:\WINDOWS\system32\npf_mgm.exe
C:\WINDOWS\system32\daemon_mgm.exe
C:\WINDOWS\system32\NetMonInstaller.exe
C:\WINDOWS\system32\rpcapd.exe
C:\WINDOWS\system32\capinstall.exe
修改注册表:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\Currentversion\Run
"wosa" = %TEMP%WOSO.EXE
"mhsa" = %TEMP%MHSO.EXE
"Microsoft Autorun14" = %SYSTEM%\ZTINETZT.EXE
"rxsa" = %TEMP%RXSO.EXE
"qjsa" = %TEMP%QJSO.EXE
"Microsoft Autorun9" = %SYSTEM%\RAVASKTAO.EXE
"tlsa" = %TEMP%TLSO.EXE
"dasa" = %TEMP%DASO.EXE
"wlsa" = %TEMP%WLSO.EXE
"wgsa" = %TEMP%WGSO.EXE
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\Run
"visin" = %SYSTEM%\VISIN.EXE
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\ShellExecuteHooks
"{0EA66AD2-CF26-2E23-532B-B292E22F3266}" =
"{754FB7D8-B8FE-4810-B363-A788CD060F1F}" =
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\nm
(Display Name)Network Monitor Driver = (IMAGEPATH)SYSTEM32\DRIVERS\NMNT.SYS
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NPF
(Display Name)NetGroup Packet Filter Driver = (IMAGEPATH)SYSTEM32\DRIVERS\NPF.SYS
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\rpcapd
(Display Name)Remote Packet Capture Protocol v.0 (experimental) = (IMAGEPATH)"%PROGRAMFILES%\WINPCAP\RPCAPD.EXE" -D -F "%PROGRAMFILES%\WINPCAP\RPCAPD.INI"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\nm
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\nm.sys
HKEY_LOCAL_MACHINE\Software\Classes\CLSID\{0EA66AD2-CF26-2E23-532B-B292E22F3266}
HKEY_LOCAL_MACHINE\Software\Classes\CLSID\{425882B0-B0BF-11CE-B59F-00AA006CB37D}
HKEY_LOCAL_MACHINE\Software\Classes\CLSID\{754FB7D8-B8FE-4810-B363-A788CD060F1F}
HKEY_LOCAL_MACHINE\Software\Classes\CLSID\{944AD531-B09D-11CE-B59C-00AA006CB37D}
HKEY_LOCAL_MACHINE\Software\Classes\CLSID\{D413C502-3FAA-11D0-B254-444553540000}
杀毒方法:
将瑞星病毒库升至2007-06-21后可杀,之前一直查不出来!

评论: 1 | 引用: 0 | 查看次数: 9319
发表评论
请登录后再发表评论!



 上一篇:
上一篇:  下一篇:
下一篇:  文章来自:
文章来自:  Tags:
Tags:  最新日志:
最新日志:

